privacyIDEA Authenticator App Version 4.3.0 released

NetKnights GmbH has released version 4.3.0 of the privacyIDEA Authenticator app. New features have been added, such as the import of tokens and a new search function.
privacyIDEA Credential Provider 3.5.0 and privacyIDEA Owncloud Plugin 3.2.0 released

NetKnights GmbH releases version 3.2 of the privacyIDEA OwnCloud Plugin and version 3.5 of the privacyIDEA Credential Provider. New features have been added to both components and existing functions have been improved.
NetKnights Customer Day 2023

In November, NetKnights invited their customers to Kassel to talk about privacyIDEA. For a whole day, multi-factor authentication was discussed in the Villa Salve, near the famous Bergpark Wilhelmshöhe. The customer day was also a platform for customers to network with each other and get to know the faces behind privacyIDEA.
Third unconference by NetKnights

Take a break from everyday business life: NetKnights is holding its third internal unconference in the countryside of Saxony-Anhalt. During these days, the team consciously takes time to talk about important content and organizational matters. In this slowed-down contrast to everyday business life, the focus is also on working together as a team.
First Internal Hackathon at NetKnights

In retreat from the daily work routine, four NetKnights developers concentrated on the work on the future release 3.8 of the privacyIDEA server.
Definition of groups for querying the second factor and forwarding the HTTP headers

IT security company NetKnights releases version 1.1.0 of the privacyIDEA Keycloak plugin. In this version, groups can be created in which it is defined who should be queried for the second factor. In this version, groups can be created in which it is defined who should be queried for the second factor.
NetKnights in search of new colleagues

Once a year, the Department of Electrical Engineering and Computer Science at the University of Kassel organizes a company fair. NetKnights used this opportunity to exchange ideas with interested students.
New user interface and simplified configuration of push tokens
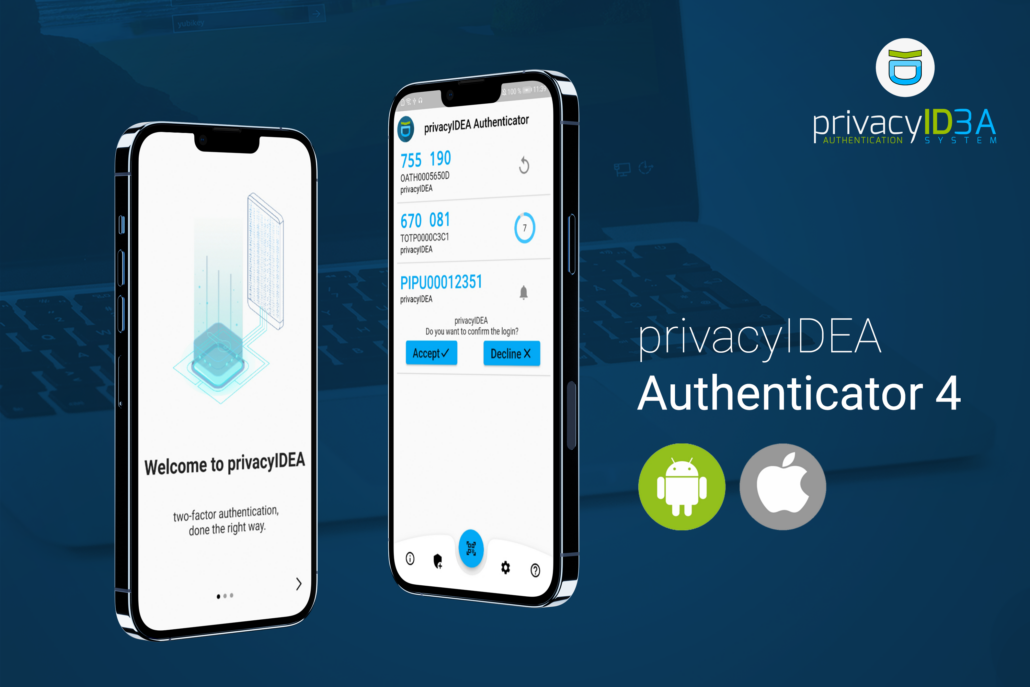
IT security company NetKnights releases version 4.0 of its privacyIDEA Authenticator app. The latest version includes simplified push token configurations, improved stability and a new user interface.
NetKnights host second internal unconference

In the middle of the Harz mountains, the NetKnights set up camp to discuss organizational and technical topics.
Multi-Factor-Authentication at the Windows desktop – also on the road
As of today the privacyIDEA Credential Provider is available in version 3.2. The offline functionality in regards to multiple users and multiple tokens was improved.
